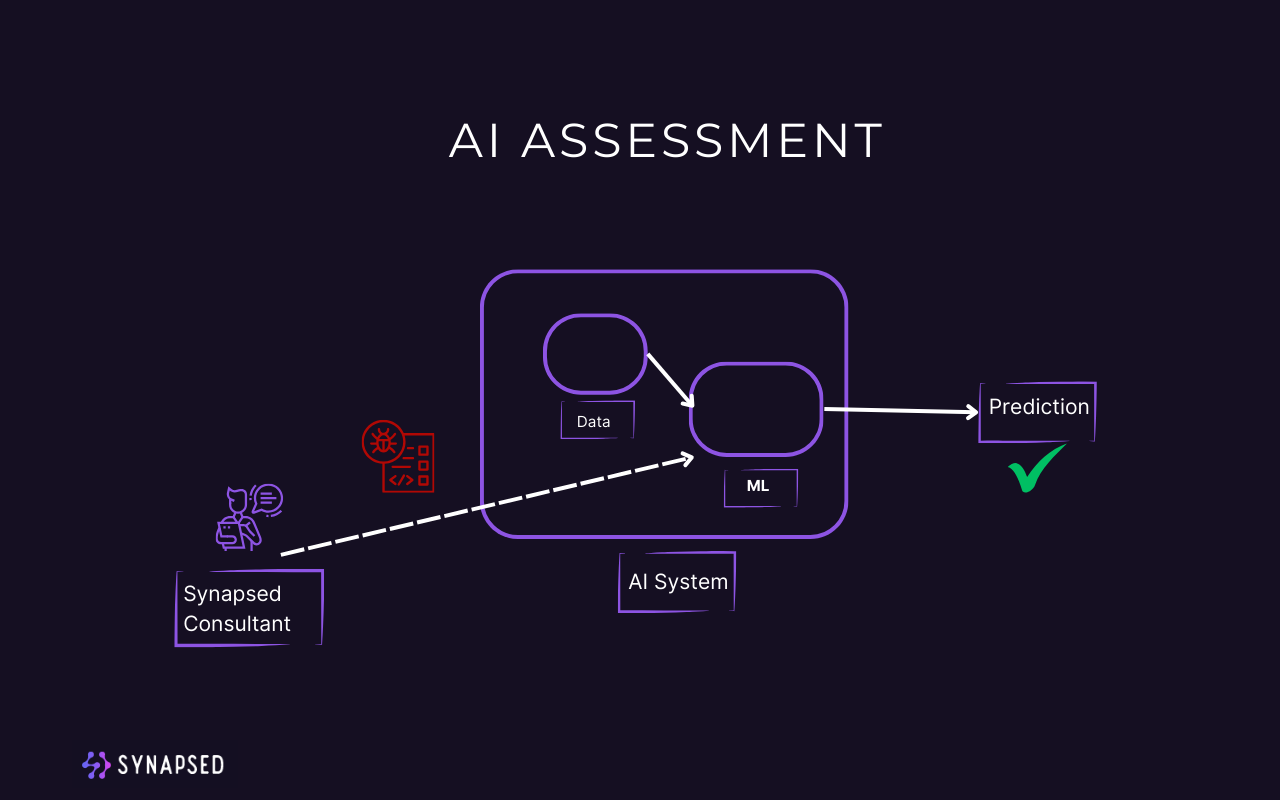
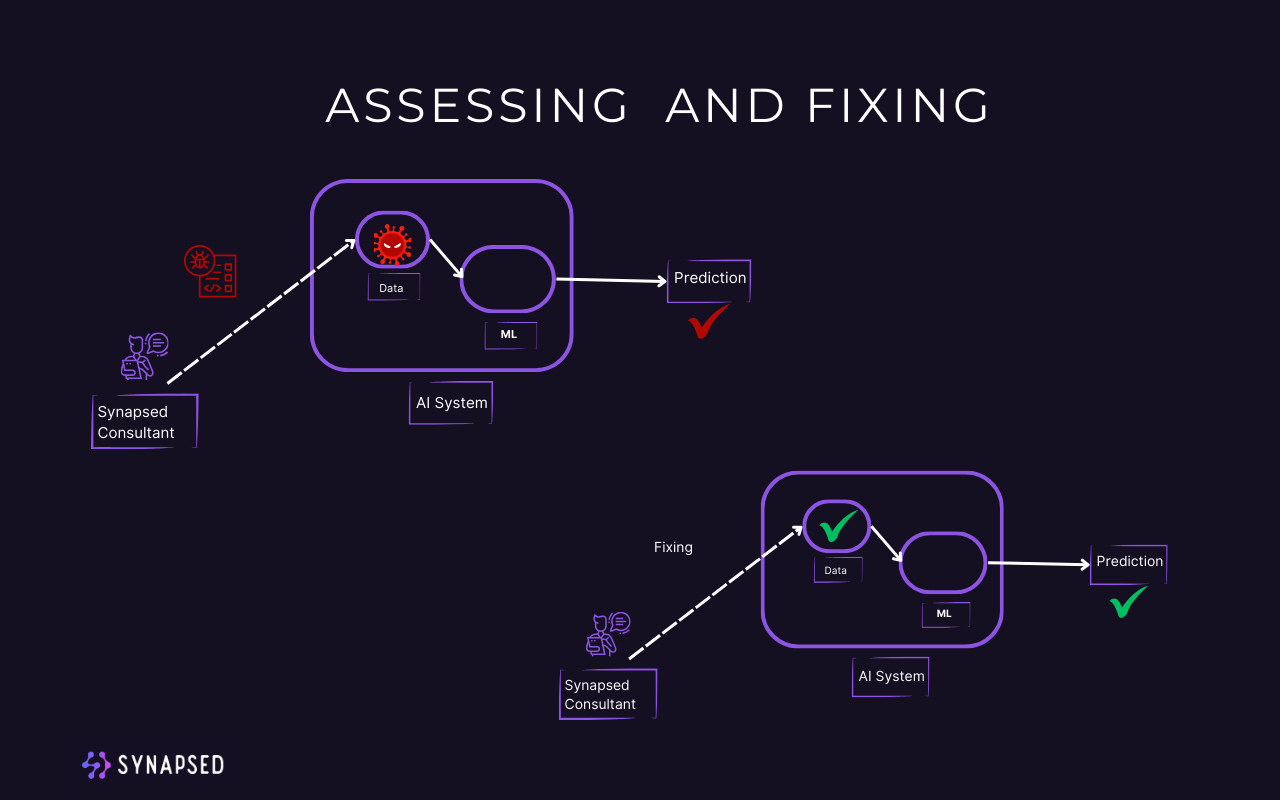
Introducing Synapsed Advanced Privacy and Security Assessment Methodology
Synapsed has leveraged its extensive experience in the privacy and security assessment of software to develop a robust methodology. This comprehensive approach is designed to safeguard your digital assets and ensure that your software systems adhere to the highest standards of data protection and cybersecurity.